
by KLEAP Technologies Pvt. Ltd. | Apr 13, 2023 | Updates
ISO 27001 is a framework for managing IT security. Though it doesn’t sound exciting, ISO 27001, is an information security management system (ISMS) that helps keep consumer data safe in all sectors and departments. It helps companies by developing a stringent...

by KLEAP Technologies Pvt. Ltd. | Apr 13, 2023 | Updates
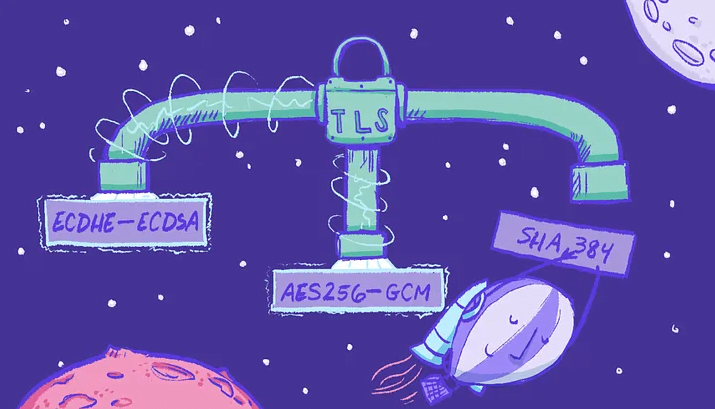
SSL (Secure Socket Layer) and TLS (Transfer Layer Protocol) are cryptographic protocols to provide security over a network. TLS is an upgraded version of SSL and is more secure providing more privacy and data integrity. When does a TLS handshake occur? Every SSL/TLS...

by KLEAP Technologies Pvt. Ltd. | Apr 13, 2023 | Updates
Ciphers! What comes to our mind when we first hear ciphers? In simple terms, a secret way of writing a code. We all know ciphers have existed for thousand of years and if I can put it in simple terms, they are set of instructions used for encrypting or decrypting a...

by KLEAP Technologies Pvt. Ltd. | Apr 13, 2023 | Updates
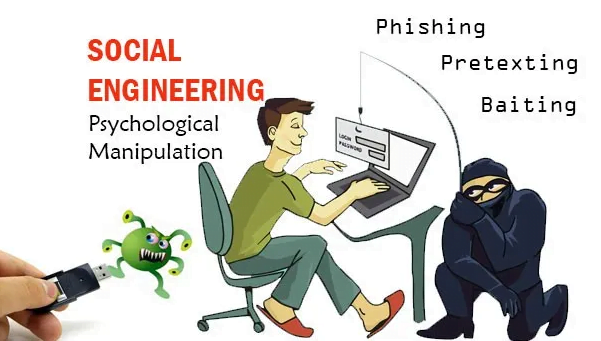
Social Engineering plays an important role in a notable number of cyberattacks. It has been consistent all through the life of internet security. But what is it exactly? In its most comprehensive sense, social engineering is about psychological manipulation — getting...

by KLEAP Technologies Pvt. Ltd. | Apr 13, 2023 | Updates
Data privacy has perpetually been essential. That is why people place locks on filing cupboards and rent safety deposit boxes at their banks. However as a lot of our information becomes digitized, and that we share a lot of information online, data privacy is...

by KLEAP Technologies Pvt. Ltd. | Apr 13, 2023 | Updates
The article was also published in Portuguese with publishing rights and maintaining authorship by Shivani Sharma by MAC Project Solutions A man-in-the-middle attack (MITM) is an attack where the attacker secretly positions himself between a user and an application and...






Recent Comments